Check out the latest business IT News.
The increasingly digitalized world we live in has a lot of benefits in business and in relationships, but with it also comes a whole new host of problems, including a rise in API data breaches. A number of high-profile companies have been affected by API data breaches in recent years, allowing other businesses to learn…
Read MoreIf you are connected to the internet, then you are a target for malware, viruses, and hackers. Every day, 350,000 new malware programs come to the surface. Your firewall and anti-virus protection can only provide so much security. That is why it is very important that you know how to spot fraudulent software and fake…
Read MoreWhat Do We Know About Terminal Fault (L1TF) Chip Vulnerabilities? Understanding The L1 Terminal Fault (L1TF) Intel has recently confirmed L1 Terminal Fault (L1TF) chip vulnerabilities in its processors that can be manipulated by malware and malevolent virtual machines with the intention of stealing private information from a computer’s memory. Who or What is Vulnerable?…
Read MoreIs It Safe For Me To Use The Airport’s Public Wi-Fi When I Travel? Most airports around the U.S. and abroad provide free Wi-Fi service to travelers stranded in their terminals, waiting for their flights. While this service may appear to be generous, a recent study by Coronet, a cybersecurity company, suggests you might want…
Read MoreUsing Rules To Organize Your Outlook 2016 Inbox The purpose of Rules in Microsoft Outlook is to help you organize your email and receive updates if items are changed. Rules can save you time, keep on top of high priority tasks, and reduce the clutter of your Outlook inbox – if you know how to…
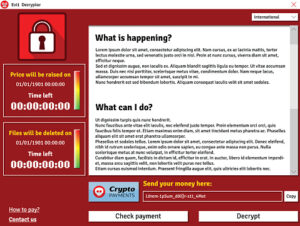
Read MoreThe Newest Forms Of Ransomware & How To Protect Your Business From Them The Situation Ransomware is now one of the top security concerns for businesses and organizations of all sizes. The City of Atlanta was hit with a ransomware attack called SamSam in March, crippling some important departments like their court system, sewer infrastructure…
Read MoreEnd-Of-Life Vs. End-Of-Sale The end of a product’s lifecycle can mean trouble for companies that haven’t prepared for the inevitable. If your organization uses certain products on a daily basis, you may find it difficult to keep up with the different dates revolving around these products’ unique life cycles. But failing to do so can…
Read MoreThey are the next best thing to hauling your laptop around to school and on flights, and they’ve become the weapon of choice for parents with fussy toddlers in public spaces. But while tablets have earned their accolades in recent years, that’s not to say choosing one to take home is an easy task. With…
Read MoreThe Microsoft Cloud for Government is a comprehensive cloud platform designed expressly for U.S. Federal, State, and Local Governments to meet the U.S. Government’s thorough security and compliance regulations. Microsoft Cloud for Government meets the standards of many government agencies, including FedRAMP, HIPAA, and CJIS, to name a few. It has the flexibility to run…
Read MorePhishing is just one of many tools in a hacker’s repertoire and happens to be one of their most effective. Through phishing, hackers dangle their bait in front of preoccupied employees who would never dream that their PC could provide an open door for a hacker. That’s why it is so important that employees understand…
Read More